A Network Bridge Filters Traffic Using Which Type Of Address?
This affiliate is from the book
5-2 The Network Bridge
A bridge can be used in computer networks to interconnect two LANs together and divide network segments. Recall that a segment is a section of a network separated past bridges, switches, and routers. The bridge is a layer 2 device in the OSI model, meaning that it uses the MAC address information to brand decisions regarding forwarding data packets. But the information that needs to be sent across the span to the adjacent network segment is forwarded. This makes it possible to isolate or segment the network data traffic. An case of using a bridge to segment two Ethernet LANs is shown in Figure 5-one. The moving-picture show shows that LAN A connects to port i of the bridge and LAN B connects to port ii on the bridge, creating two segments, as shown. There are 4 computers in LAN A and three computers in LAN B. It is of import to note that bridges are now legacy networking devices, but studying these will aid you amend understand the functionality of switches, specially how data traffic is sent to continued LANs.
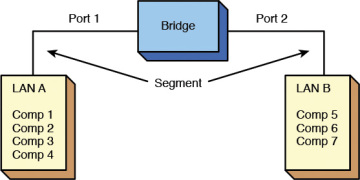
Figure 5-1 Using a span to interconnect two Ethernet LANs.
Bridges monitor all data traffic in each of the LAN segments connected to its ports. Call back that a port is an input/output connection on a networking device. The bridges use the MAC addresses to build a bridging table of MAC addresses and port locations for hosts connected to the bridge ports. A sample bridging table is provided in Table five-two. The table shows the stored MAC accost and the port where the address was obtained.
TABLE five-2 Bridging Table
| MAC Address | Port |
| 00-forty-96-25-85-BB | 1 |
| 00-40-96-25-8E-BC | i |
| 00-sixty-97-61-78-5B | 2 |
| 00-C0-4F-27-xx-C7 | two |
The source MAC address is stored in the span table as soon as a host talks (transmits a data packet) on the LAN. For example, if reckoner 1 in LAN A sends a message to computer ii (run across Figure 5-ane), the bridge will shop the MAC addresses of both computers and tape that both of these computers are connected to port 1. If computers v or 6 are placing information packets on the network, then the source MAC addresses for 5 and 6 are stored in the span tabular array and it is recorded that these computers connect to port 2 on the bridge. The MAC addresses for computers 3 and 4 will not exist added to the bridging tabular array until each transmits a data package.
The bridge monitors the data on its ports to bank check for an association betwixt the destination MAC address of the Ethernet frames to any of the hosts connected to its ports. An association indicates that the destination MAC address for a host is continued to one of the ports on the bridge. If an association is found, the data is forwarded to that port. For example, presume that figurer 1 sends a message to computer 5 (see Figure 5-1). The bridge detects an association between the destination MAC address for computer 5 and port two. The bridge and then forrad the data from computer 1 to calculator 5 in LAN B via port 2.
The adequacy of a bridge to forward data packets only when there is an clan is used to isolate data traffic in each segment. For example, assume that estimator 1 and estimator two in LAN A generate a lot of data traffic. The computers in LAN B will not encounter any of the data traffic as long as there is non an clan between the destination MAC addresses of the Ethernet packets and whatsoever of the hosts in LAN B (computers v, 6, and 7).
A potential problem with bridges has to exercise with the style broadcasts are handled. A broadcast ways the message is existence sent to all computers on the network; therefore, all broadcasts in a LAN volition be forwarded to all hosts connected within the bridged LANs. For instance, the broadcast associated with an ARP will appear on all hosts. ARP stands for Accost Resolution Protocol, which is a protocol used to map an IP address to its MAC accost. In the address resolution protocol, a circulate is sent to all hosts in a LAN connected to the bridge. This is graphically shown in Effigy five-two. The bridge forwards all broadcasts; therefore, an ARP asking broadcasting the message "Who has this IP address?" is sent to all hosts on the LAN. The data packets associated with ARP requests are small, but information technology requires computer time to process each request. Excessive amounts of broadcasts beingness forwarded by the bridge tin lead to a broadcast tempest, resulting in degraded network performance, chosen a network slowdown.
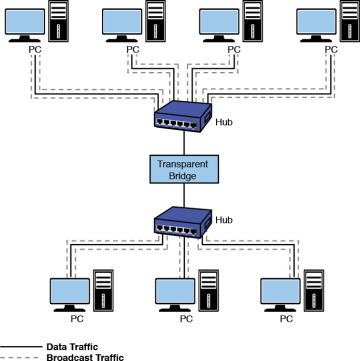
FIGURE 5-2 An instance of using a bridge to isolate information traffic.
The MAC address entries stored in a span table are temporary. Each MAC address entry to the bridge table remains active every bit long as there is periodic data traffic action from that host on its port. However, an entry into the table is deleted if the port becomes inactive. In other words, the entries stored into the table have a limited lifetime. An expiration timer will embark one time the MAC accost is entered into the bridge tabular array. The lifetime for the entry is renewed past new data traffic by the calculator, and the MAC address is reentered.
In a like manner, all networking devices (for case, computers) contain an ARP cache, a temporary storage of MAC addresses recently contacted. This is also called the ARP table. The ARP cache holds the MAC address of a host, and this enables the message to be sent directly to the destination MAC accost without the computer having to issue an ARP asking for a MAC accost. The following list outlines typical steps of a communication process between computer 1 and reckoner 2.
- Computer 1 checks its ARP cache to make up one's mind if it already has the MAC address of calculator 2. If it does, information technology will skip to the final stride; otherwise, information technology proceeds to the adjacent step.
- Computer 1 generates an ARP request message for calculator 2 with its own MAC and IP information included.
- Computer 1 then broadcasts the ARP request message on its local network.
- Every local network device processes the ARP request message. Those computers that are not computer 2 will discard the message.
- Only a friction match, which is reckoner 2, generates an ARP reply message and updates its ARP cache with computer i MAC and IP information.
- Calculator ii sends an ARP reply bulletin straight to estimator 1.
- Computer ane receives the ARP reply message and updates its ARP cache with the MAC and IP of computer two.
The ARP enshroud contents on a Windows reckoner can be viewed using the arp -a control while in the command prompt, as shown here:
| Windows | Mac OS X | ||
| C:\arp -a | jmac:~mymac$ arp -a | ||
| Interface: 10.x.20.2 on Interface x1000002 | C1.salsa.org (192.168.12.1) at | ||
| Net Address | Physical Address | Type | 00-08-a3-a7-78-0c on en1 |
| x.10.20.3 | 00-08-a3-a7-78-0c | dynamic | [ethernet] |
| 10.10.20.iv | 00-03-ba-04-ba-ef | dynamic | C3.salsa.org (192.168.12.1) at |
| 00-08-a3-a7-78-0c on en1 | |||
| [ethernet] | |||
The ARP cache contents on a Mac Bone X computer tin exist viewed using the arp -a command while in the terminal mode.
The following bulletin is generated if all the ARP entries accept expired:
c:\arp -a No ARP Entries Establish
The name for the type of span used to interconnect ii LANs running the same type of protocol (for example, Ethernet) is a transparent bridge. Bridges are as well used to interconnect two LANs that are operating 2 different networking protocols. For example, LAN A could be an Ethernet LAN and LAN B could be a token ring. This blazon of bridge is called a translation bridge. An case is provided in Effigy 5-3. The span allows data from one LAN to be transferred to some other. Also the MAC addressing information is standardized so the same address data is used regardless of the protocol.
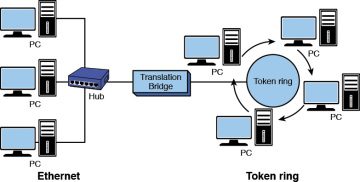
Figure five-iii Using a translation span to interconnect an Ethernet and token-band LAN.
A mutual application today using a span is interconnecting LANs using wireless technology. The employ of wireless bridges in LANs is a popular choice for interconnecting the LANs when the toll of physically connecting them is prohibitive. Wireless technology and its LAN applications were presented in Affiliate iv, "Wireless Networking."
The utilize of a bridge is not as mutual equally information technology used to be except for wireless network applications. New networking technologies are available that provide similar capabilities to the bridge but that are much more than powerful. However, the bridge still is useful and has several advantages. Tabular array 5-three provides a summary of the advantages and disadvantages of a networking span.
TABLE five-three Summary of the Advantages and Disadvantages of a Bridge for Interconnecting LANs
| Advantages | Disadvantages |
| Like shooting fish in a barrel to install | Works all-time in low-traffic areas |
| Does an splendid chore of isolating the information traffic in ii segments | Forwards broadcasts and is susceptible to broadcast storms |
| Relatively inexpensive | |
| Can be used to interconnect 2 LANs with different protocols and hardware | |
| Reduces collision domains (remember how the CSMA/CD protocol works) |
A Network Bridge Filters Traffic Using Which Type Of Address?,
Source: https://www.pearsonitcertification.com/articles/article.aspx?p=2474237&seqNum=2
Posted by: mirandalacceir.blogspot.com


0 Response to "A Network Bridge Filters Traffic Using Which Type Of Address?"
Post a Comment